A team of engineers from the Southwest Research Institute (SwRI) in Texas has successfully hacked an electric vehicle while it charged to demonstrate cybersecurity vulnerabilities.
As part of a simulated malicious attack, the SwRI team reverse-engineered the signals and circuits on an EV and a charger to disrupt the vehicle charging.
A ‘man-in-the-middle’ (MITM) spoofing device, developed in a laboratory using low-cost hardware and software, was able to disturb signals between the charger and vehicle.
SwRI performed three manipulations: limiting the rate of charging, blocking battery charging and overcharging.
Austin Dodson, an SwRI engineer who led the research, said: “The project effectively tricked the test vehicle into thinking it was fully charged and also blocked it from taking a full charge.”
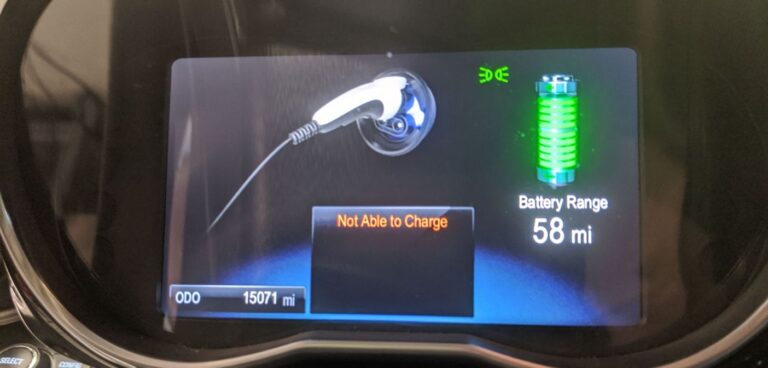
According to Dodson, while overcharging, the vehicle battery management system detected a power level that was too high and automatically disconnected from charging. To limit charging, the MITM device requested the smallest charge allowed – 6A – to reduce the charging rate. To block battery charging, a proximity detection signal barred charging and displayed the warning “Not Able to Charge”.
It’s believed that cybersecurity issues related to charging infrastructure will be increasingly important as demand for EVs grows.
Victor Murray, an SwRI engineer and team lead in the critical systems department, added: “Discovering vulnerabilities in the charging process demonstrates opportunities for testing standards for electric vehicles and charging infrastructure.”
SwRI is researching several automotive cybersecurity initiatives for automated and connected vehicles, intelligent transportation systems and IoT networking devices.